Terminal Resign Codesign Mac App Example
Jun 07, 2017 New Issue Checklist. Updated fastlane to the latest version; I have read the Contribution Guidelines; Issue Description. We have a White label app that we build once, and then use act to change configs, assets, info.plist. We use act and resign to create. In the Terminal app on your Mac, enter the complete pathname of the tool’s executable file, followed by any needed arguments, then press Return. If a command is located in one of the shell’s known folders, you can omit path information when entering the command name.
- If your app accesses certain features of iOS (for example, push notifications), you must create an entitlements file. For more information about creating an entitlements file, see Creating an iOS entitlements file.
- Oct 05, 2016 If we want to resign a simple iOS app the first thing we’ll need it’s an Apple certificate installed in our Keychain and a Provisioning Profile linked to it. For this process we’ll need to have Xcode in our Mac. We’ll start decompressing the.ipa file, for that we open a terminal in the path where we have stored the ipa and we execute the following command.
- For example, Awesome Live Chat Desk OS X lets you provide your customers with live chat support via simple Mac notifications. Also, before we start tinkering around with it, it is probably worth taking a couple of minutes to tell you exactly what Terminal is (all in a non-technical sense, of course!). Terminal.app running under OS X (Lion).
Code signing is a macOS security technology that you use to certify that an app was created by you. Once an app is signed, the system can detect any change to the app—whether the change is introduced accidentally or by malicious code.
You participate in code signing as a developer when you obtain a signing identity and apply your signature to apps that you ship. A certificate authority (often Apple) vouches for your signing identity.
Note: In most cases, you can rely on Xcode’s automatic code signing, which requires only that you specify a code signing identity in the build settings for your project. This document is for readers who must go beyond automatic code signing—perhaps to troubleshoot an unusual problem, or to incorporate the codesign(1) tool into a build system.
Benefits of Code Signing
After installing a new version of a code-signed app, a user is not bothered with alerts asking again for permission to access the keychain or similar resources. As long as the new version uses the same digital signature, macOS can treat the new app exactly as it treated the previous one.
Other macOS security features, such as App Sandbox and parental controls, also depend on code signing. Specifically, code signing allows the operating system to:
Ensure that a piece of code has not been altered since it was signed. The system can detect even the smallest change, whether it was intentional (by a malicious attacker, for example) or accidental (as when a file gets corrupted). When a code signature is intact, the system can be sure the code is as the signer intended.
Identify code as coming from a specific source (a developer or signer). The code signature includes cryptographic information that unambiguously points to a particular author.
Determine whether code is trustworthy for a specific purpose. Among other things, a developer can use a code signature to state that an updated version of an app should be considered by the system to be the same app as the previous version.
Limitations of Code Signing
Code signing is one component of a complete security solution, working in concert with other technologies and techniques. It does not address every possible security issue. For example, code signing does not:
Guarantee that a piece of code is free of security vulnerabilities.
Guarantee that an app will not load unsafe or altered code—such as untrusted plug-ins—during execution.
Provide digital rights management (DRM) or copy protection technology. Code signing does not in any way hide or obscure the content of the signed code.
See Also
Read Security Overview to understand the place of code signing in the macOS security picture.
For descriptions of the command-line tools for performing code signing, see the codesign and csreq man pages.
Copyright © 2016 Apple Inc. All Rights Reserved. Terms of Use Privacy Policy Updated: 2016-09-13
-->Yes, it is possible but it will usually require that you re-sign the .app bundle after making the change.
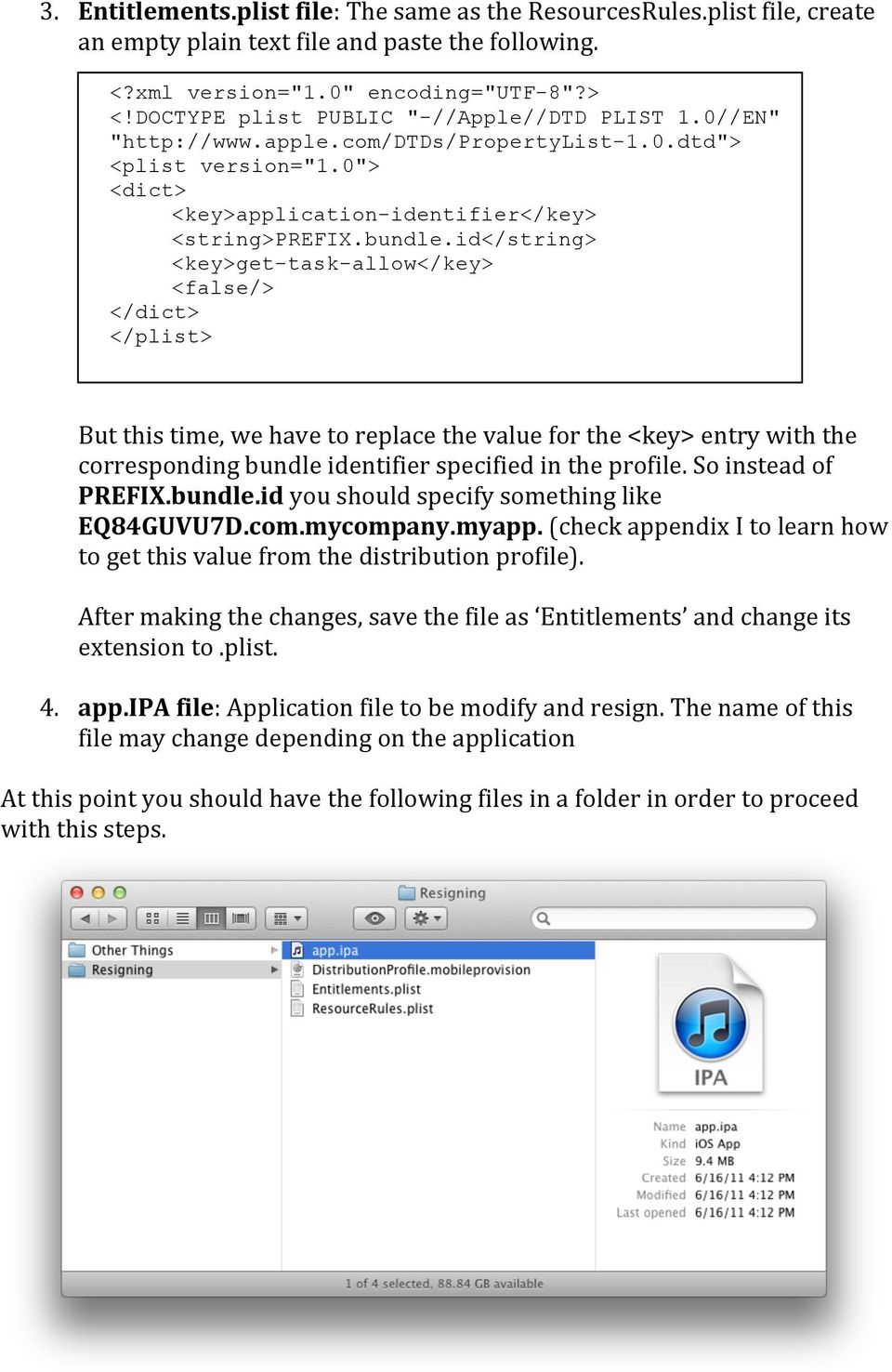
Note that modifying the .ipa file is not necessary in normal use. This article is provided purely for informational purposes.
Example: removing a file from a .ipa archive
For this example assume that the name of the Xamarin.iOS project is iPhoneApp1 and the generated session id is cc530d20d6b19da63f6f1c6f67a0a254

Build the
.ipafile as normal from Visual Studio.Switch over to the Mac build host.
Find the build in the
~/Library/Caches/Xamarin/mtbs/buildsfolder. You can paste this path into Finder > Go > Go to Folder to browse the folder in Finder. Look for the folder that matches the project name. Within that folder, look for the folder that matches thegenerated session idof the build. This will most likely be the subfolder that has the most recent modification time.Open a new
Terminal.appwindow.Would recommend for anyone who needs to keep track of songs they write for their band or just for yourself. No monthly subscription, and the “premium” version is decently priced. Vendettakid648, Great app, just needs a couple more thingsThis is a great app, it just needs a couple more things to accommodate more guitarists needs.

Type
cdinto the Terminal.app window, and then drag & drop thegenerated session idfolder into theTerminal.appwindow:Type the return key to change directory into the
generated session idfolder.Unzip the
.ipafile into a temporaryold/folder using the following command. Adjust theAd-HocandiPhoneApp1names as needed for your particular project.ditto -xk bin/iPhone/Ad-Hoc/iPhoneApp1-1.0.ipa old/
Keep the
Terminal.appwindow open.Delete the desired files from the
.ipa. You can either move them to the Trash using Finder, or delete them on the command line usingTerminal.app. To view the contents of thePayload/iPhonefile in Finder, Control-click the file and select Show Package Contents.Using the same general approach as in step 3, find the log file under
~/Library/Logs/Xamarin/MonoTouchVS/that has both the project name and thegenerated session idin the name:Open the build log from step 10, for example by double-clicking it.
Find the line that includes
tool /usr/bin/codesign execution started with arguments: -v --force --sign.Type
/usr/bin/codesigninto the Terminal.app window from step 8.Copy all of the arguments starting with
-vfrom the line in step 12, and paste them into the Terminal.app window.Change the last argument to be the
.appbundle located within theold/Payload/folder, and then run the command.Change into the
old/directory in Terminal:Zip up the contents of the directory into a new
.ipafile using thezipcommand. You can change the'$HOME/Desktop/iPhoneApp1-1.0.ipa'argument to output the.ipafile wherever you'd like:
Common error messages
If you see Invalid Signature. A sealed resource is missing or invalid., that generally means that something was changed within the .app bundle, and that the .app bundle was not correctly re-signed afterwards. Also note that if you wish to create an .ipa with a distribution profile, you must build the original .ipa with a distribution profile. Otherwise the Entitlements.xcent will be incorrect.
To give a concrete example of how this error can arise, if you run the following codesign --verify command in the Terminal window after step 9, you will see the error along with the precise cause of the error:
Codesign Man Page
And the App Store verification process will report a similar error message:
Mac Codesign Command Line
ERROR ITMS-90035: 'Invalid Signature. A sealed resource is missing or invalid. The binary at path [iPhoneApp1.app/iPhoneApp1] contains an invalid signature. Make sure you have signed your application with a distribution certificate, not an ad hoc certificate or a development certificate. Verify that the code signing settings in Xcode are correct at the target level (which override any values at the project level). Additionally, make sure the bundle you are uploading was built using a Release target in Xcode, not a Simulator target. If you are certain your code signing settings are correct, choose 'Clean All' in Xcode, delete the 'build' directory in the Finder, and rebuild your release target. For more information, please consult https://developer.apple.com/library/ios/documentation/Security/Conceptual/CodeSigningGuide/Introduction/Introduction.html'